Phishing Email Examples
Phishing emails prey upon our lax attention. Here are some of the tactics used in common phishing email attacks.
Things to Verify
Verify sender address
Even though sender email addresses can be spoofed to appear from a legitimate source, you should verify that the sender’s address is what you expect.
|
Note
|
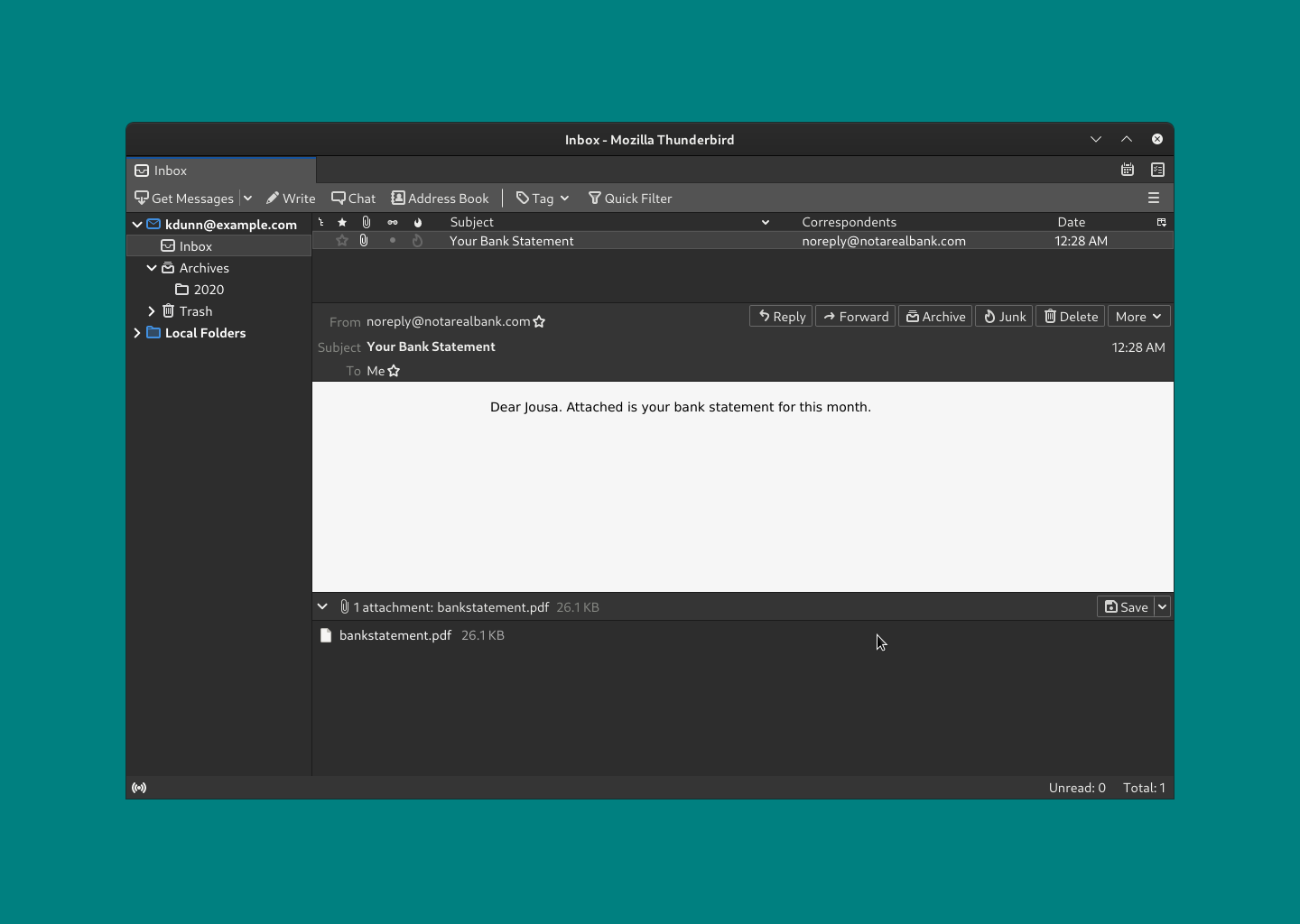
Legitimate Address
Note that the sender address in this legitimate email from Comcast/Xfinity has a |
|
Caution
|
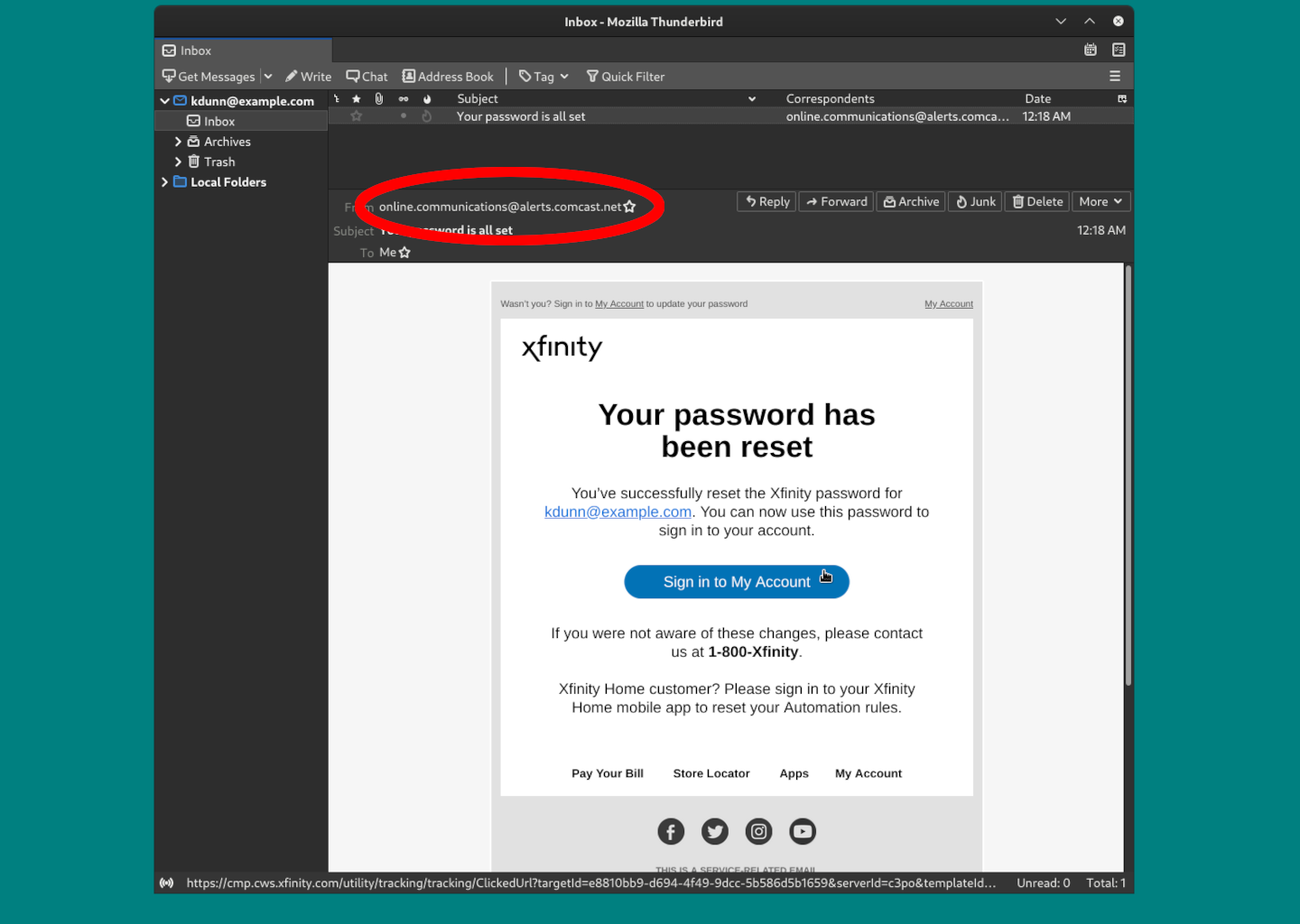
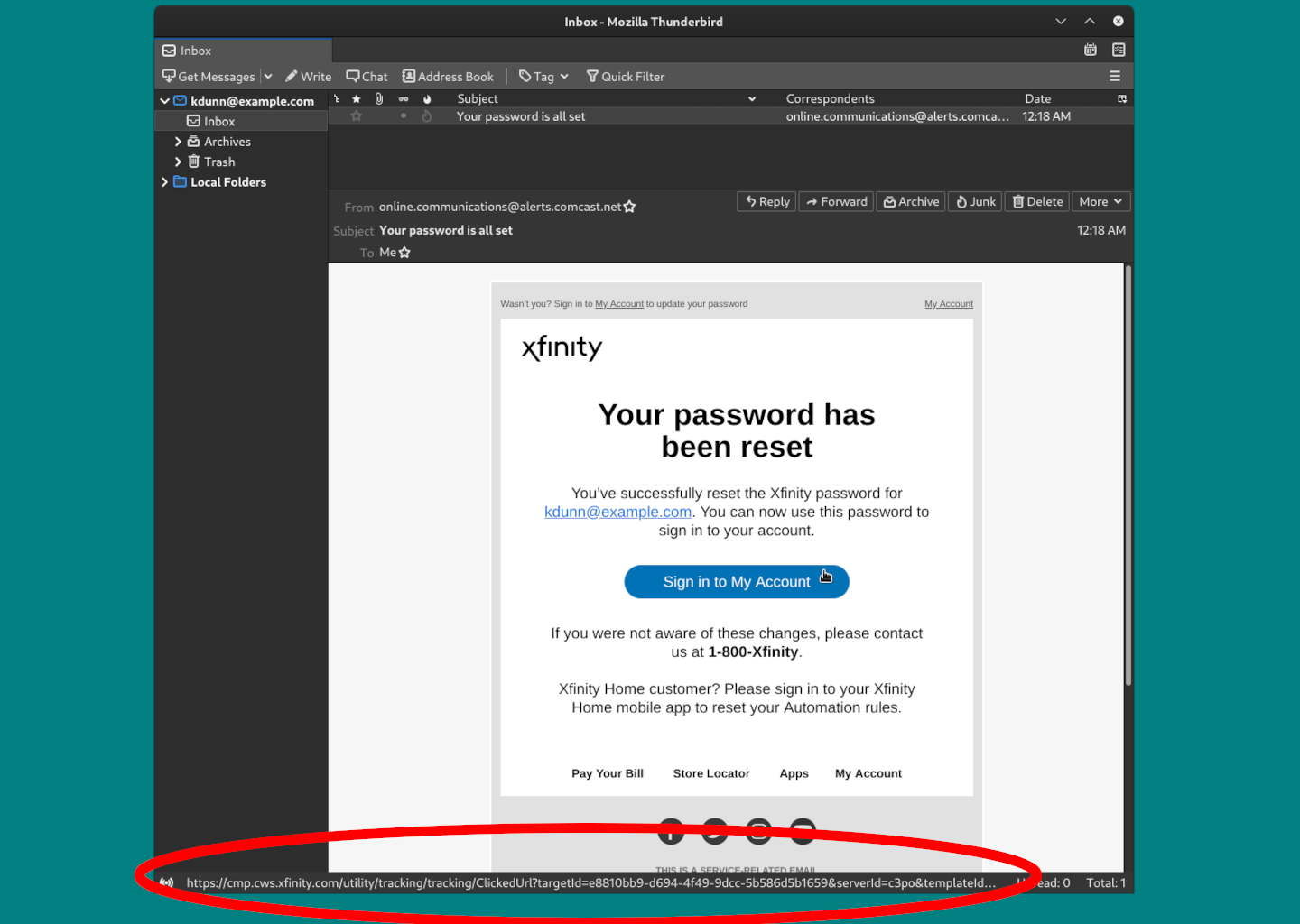
Legitimate Address; Phishing Email
Note that the sender address in this phishing email also uses a You should still verify the addresses of links before you click them. Look at the URL on the bottom of the image to verify. |
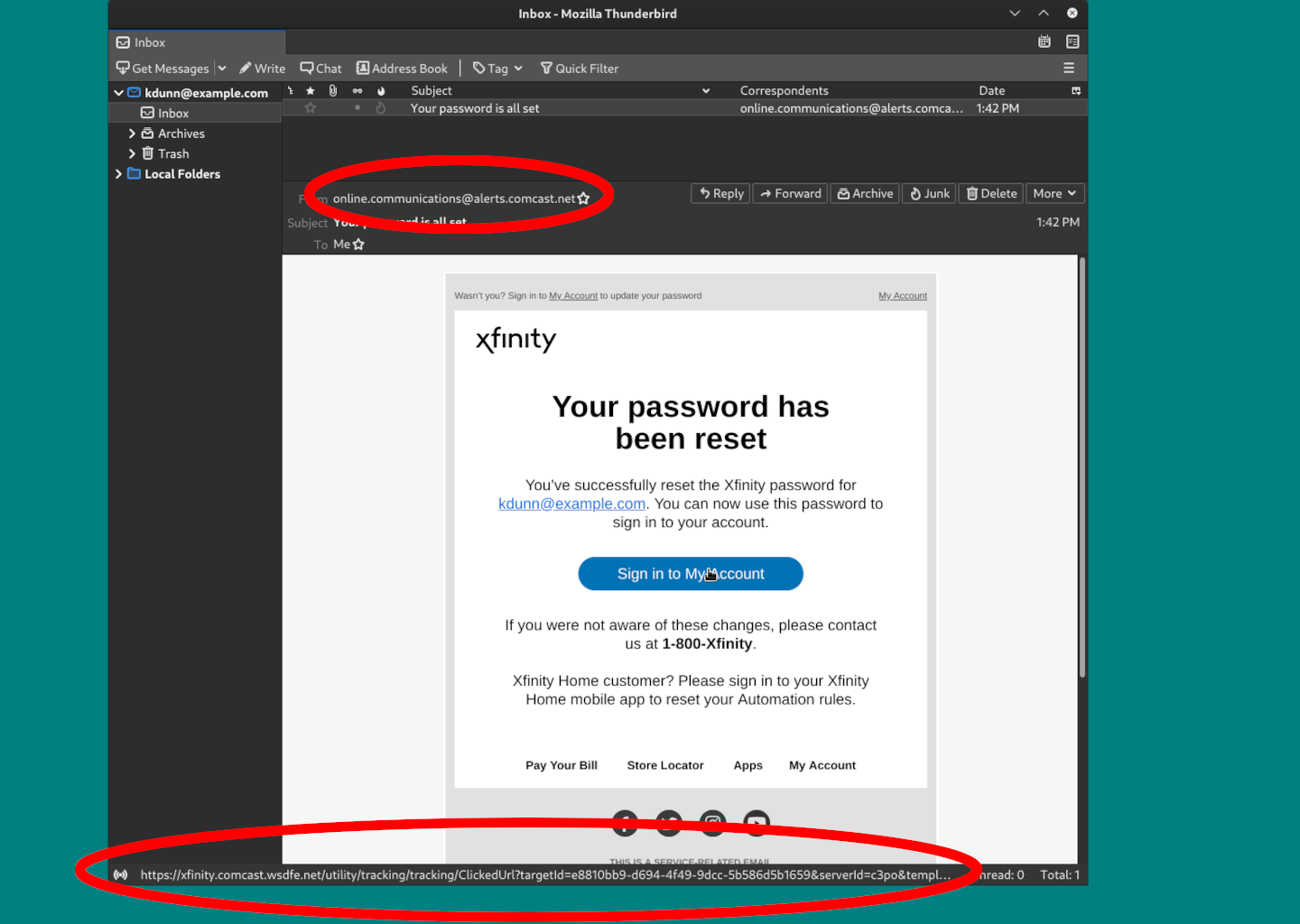
Verify URL Destinations
Phishing emails use links to send you to websites where while they look legitimate, they are not legitimate.
Use your mouse to hover over links or long-press on a touch-based device to show where the link will send you before you click on it.
Attackers hide dangerous links in the following ways:
-
Using a "look-alike" domain,
comcast.com.rse2d34s.attacker.urlinstead ofcomcast.com, for example -
Using URL shortener to hide URLs.
-
Something like
tinyurl.comor the like.
-
|
Note
|
Legitimate Email; Legitimate Link
Hover over or long-press the link or button before you press it. This email has safe links as they point to an |
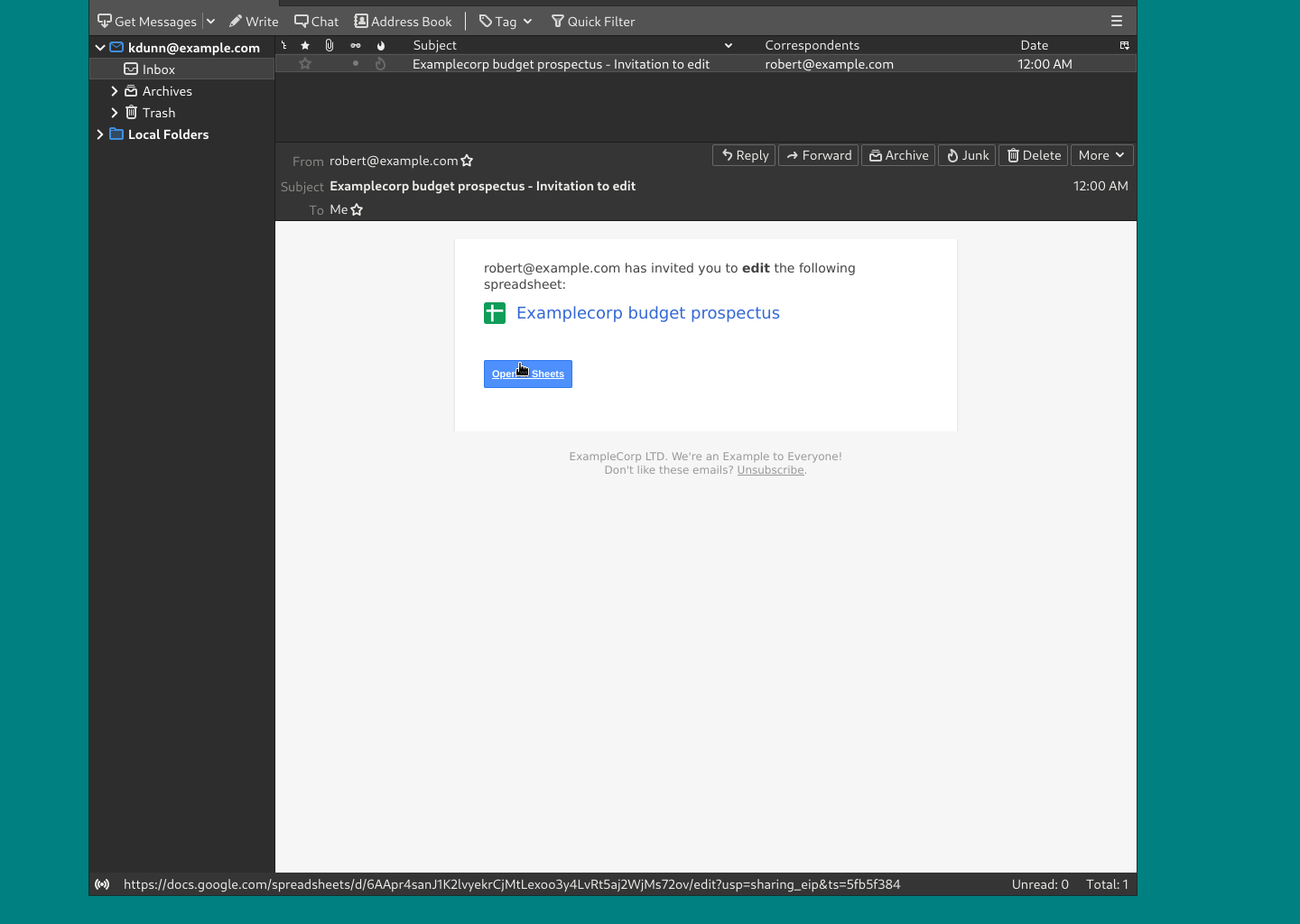
Example of a legitimate email from Google Docs
|
Note
|
Legitimate Email; Google Docs
Hover over or long-press the link or button before you press it. This email has safe links as they point to a |
|
Caution
|
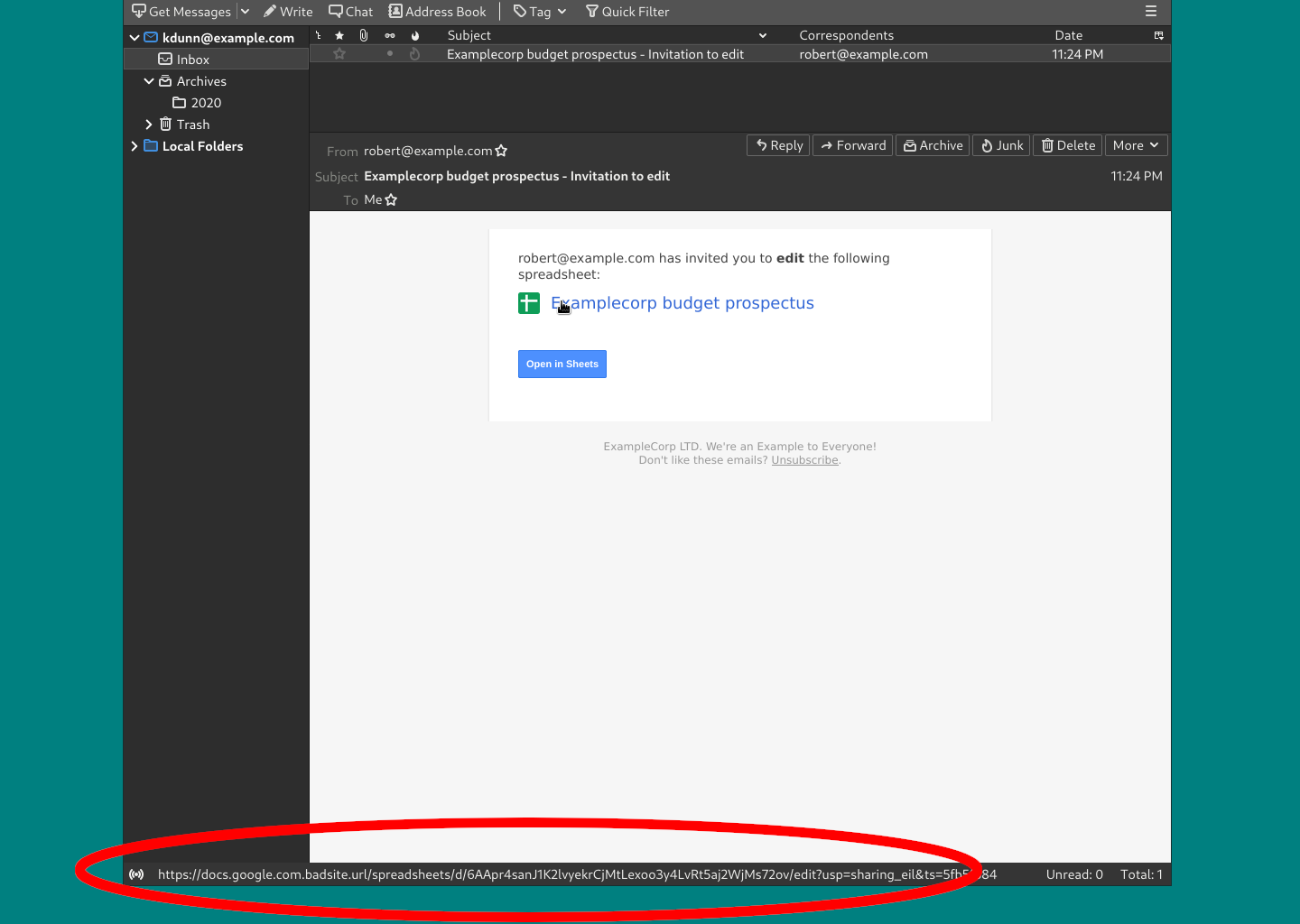
Phishing Email; Google Docs
Compare the above email to this one. This email does not have safe links as they point to a |
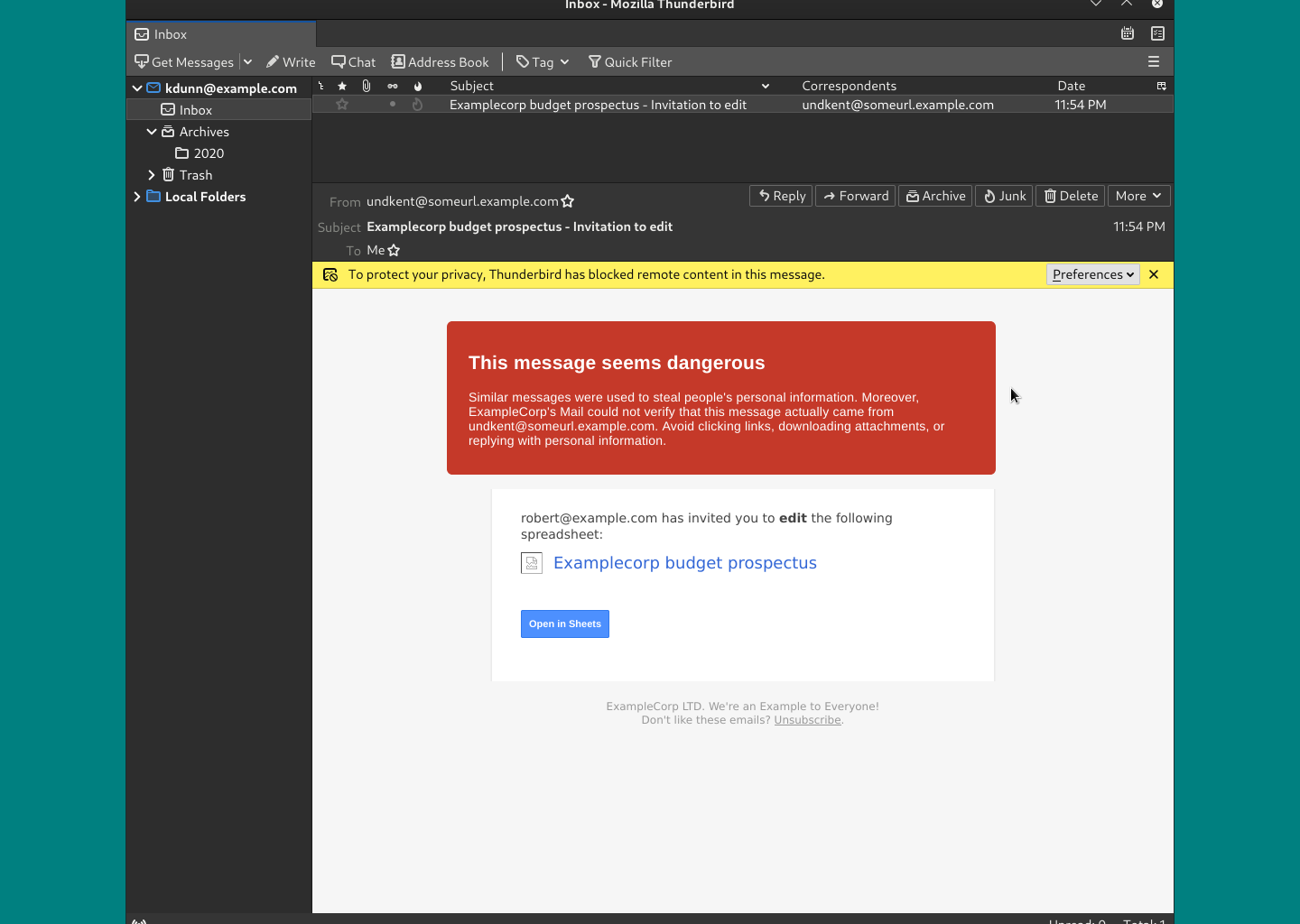
Trust Your Email Provider and Email Client Warnings
Often you will get warnings either from your email provider or the email client itself.
You should trust those warnings and give any email containing said warnings a thorough vetting.
Verify Attachments are Expected
Computer Viruses and malware are often included in attachments.
You should not open an attachment you are not expecting, even if it is from a contact you know and trust.